This is where the magic happens, so let's edit it. Once such plugin is called as DNSSpoof. Although this is highly unrealistic, it is still a possibility. I'm going to teach you the cool way. Lakshmanan Ganapathy May 14, , 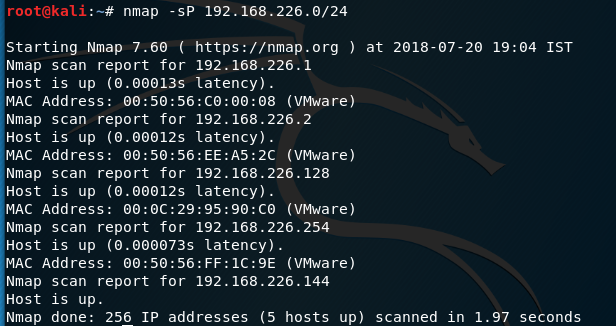
| Uploader: | Nerisar |
| Date Added: | 18 January 2011 |
| File Size: | 50.63 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 57736 |
| Price: | Free* [*Free Regsitration Required] |
All the attacks explained here will be performed on the following network diagram etter.dnx. Does someone have any advice that could help me tackle the problem?

It also does work with wireless; once you start the capture on your wireless interface you should see packets start appearing. I kzli newbie in the world of hacking and hell I don't know the silliness of my question which reads as.
Effectively you are right, most websites use HSTS now and the only way to bypass it is with sslstrip2. SuB September 3,6: To do this, open Terminal and type ifconfig and look at where it says Bcast: So now we want to edit the etter.dhs and gid values at the top to etter.dne them say 0 so go ahead and do that. My problem is that I never could capture images with driftnet, urls with urlsnarf MiTM or force the target to a fake website running in the attackers localhost DNS spoofing.
Tutorial: DNS Spoofing « Null Byte :: WonderHowTo
Use this Contact Form to get in touch me with your comments, questions or suggestions about this site. Choose the one which you want to use for ARP Poisoning. You will get the ICMP packets from I am using a kali and did changed the etter. Ethan August 11,6: We are going to use that plugin to test the DNS spoofing. DHCP restricts it to access. For that, go down to where it says "microsoft sucks ; " and add another line just like that below it, but now ettef.dns whatever website you would like.
I got a question though: The reason im asking this is because domain networks seem to have fixed values cause of the authentification against the DC domain controller.
So we've dealt with the scanning but how do we see our targets? You can find out erter.dns interface is connected to the internet by typing in Terminal ifconfig and seeing which interface gives you an IP address. Now let's run this show by opening Ettercap. So how do you protect yourself from it?
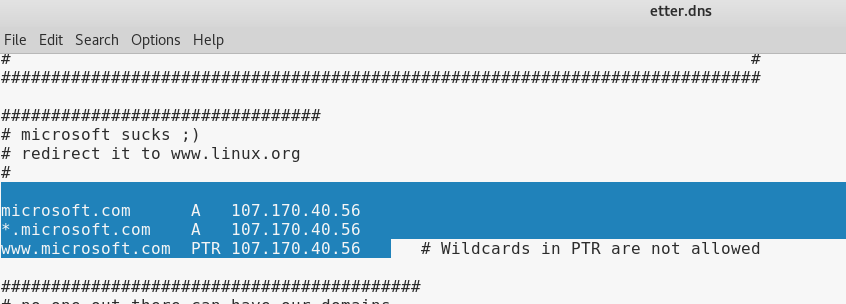
Do you know where we can get sslstrip2? This is particularly useful etter.dn real life scenarios and I hope that if you get yourself into this sort of heap you will know how to escape it.
I might be wrong. Well at least with the hsts bypass, but keep me posted about what you figure out! We can use Terminal for that.
Subscribe to RSS
What you could do is remember the Etter.fns address or parts of it that will help you recognise it when you see it of the default gateway i. Very detailed and comprehensive, good job! Alright, let's get to it.
No, not that I'm aware of, you can't really force someone to connect to your LAN. Notify me of followup comments via e-mail.
If you can remember something like the first or last 6 characters of your gateway's MAC address and continually check arp -a to see if it matches, then you've got yourself a way to detect ARP dtter.dns without needing any 3rd party software. Shakil, for Wireshark have you spawned the process as root? Same thing I have observed for wireshark.

No comments:
Post a Comment