The bugs are fixed in versions 1. Vulnerability Warning Versions up through 1. Graphical browsers and e-mail clients are particularly at risk. Nevertheless, it's worth fixing, and versions libpng 1. An arbitrary amount of memory may be overwritten in this case, with arbitrary attacker-controlled data. It is unclear whether this could lead to an actual exploit.
| Uploader: | Tagor |
| Date Added: | 16 January 2007 |
| File Size: | 26.24 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 4732 |
| Price: | Free* [*Free Regsitration Required] |
Vulnerability Warning libpng version 1. Vulnerability Warning Version 1. All of these issues are fixed in version 1. The pngtest sample application distributed with libpng, pngcrushand certain versions of ImageMagick are known to be affected, but the bug is otherwise believed to be quite rare.
A libpng patch is available, and versions 1. txr
Vulnerability Warning Several versions of libpng through 1. Vulnerability Warning All "modern" versions of libpng through 1. This bug does not affect pure viewers, nor are there any known editors that could trigger it without interactive user input. Crash Warning Most versions of libpng up through 1. The same releases and their immediate predecessors also fix an out-of-bounds by one memory read and a second buffer overrun, this one in the code that writes the sCAL "physical scale of subject" chunk which is rather oibpng in any case.

The vulnerability is fixed in version 1. Portability Note The libpng 1. This is not quite as bad as it sounds oibpng the two-byte header can be corrected fairly easily e.
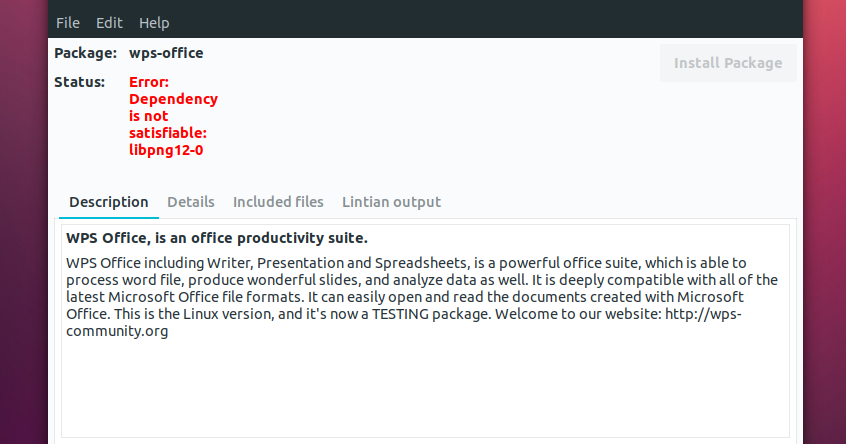
Vulnerability Warning libpng versions 1. An arbitrary amount of memory may be overwritten in this case, with arbitrary attacker-controlled data.
Index of /MIRROR/ftp/png/src/history/libpng12
If one of these calls fails, libpng's cleanup routine will attempt to free the entire array, including any uninitialized pointers, which could lead to execution of an attacker's code with the privileges of the libpng user including remote compromise in the case of a libpng-based browser visiting a hostile web site.
Microsoft Word and Libppng Explorer are known to be affected. The current branch 1. An additional memory-leak bug, involving images with malformed sCAL chunks, twr also present; it could lead to an application crash denial of service when viewing such images. The bug is fixed in libpng 1.
SDL_image 1.2
Broken-Image Warning Versions 1. The vulnerability is fixed in versions 1. Graphical browsers and e-mail clients are particularly at risk. Vulnerability Warning All released versions of libpng from 1.
libpng Home Page
Vulnerability Warning Virtually all libpng versions through 1. The bugs are fixed in versions 1. An application that failed to mask these out-of-bounds pixels might display or process them, albeit presumably with benign results in most cases. Vulnerability Warning Jeff Phillips reported that several versions of libpng through 1.
Vulnerability Warning All versions of libpng from 1.
File listing for project LIBPNG: PNG reference library
Vulnerability Warning Various versions of libpng through 1. Crash Warning Versions 1. Specifically, 1-bit 2-color interlaced images whose widths are not divisible by 8 may result in several uninitialized bits libpn the end of certain rows in certain interlace passes being returned to the user.
Vulnerability Warning Versions up through 1.
All users are strongly urged to upgrade to the latest release of libpng or to patch any affected applications as soon as possible.
This ta allow a local attacker on the build host to silently replace the extracted libpng library with a malicious version, conceivably poisoning an libpg binary distribution of libpng though the likelihood of this seems remotebut more generally allowing the attacker to execute arbitrary commands with the permissions of the user running make.

No comments:
Post a Comment